Bot Protection
Web scraping bots drive your business to loss by brute-force hacking, identity theft, creating useless traffic and competitive parsing on websites.
Protect your web application from the most sophisticated bot attacks with Qrator Bot Protection.
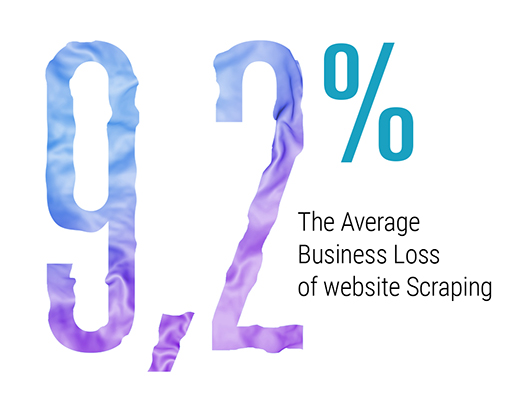
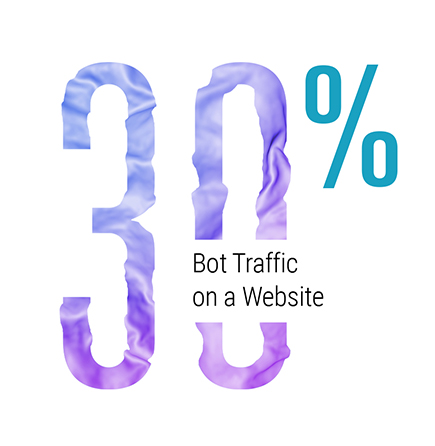
How bad bots can affect your business
SCRAPING
Automated content scraping activities are used for extracting data from websites.
Qrator Bot Protection blocks malicious activity by analyzing user fingerprinting by means of JavaScript code. This approach allows transparency for legitimate users with minimal added delay in traffic processing.
BRUTE FORCE ATTACKS
A brute force attack uses trial-and-error to guess login info, encryption keys, secret links, promo codes, or any additional information you would not like to make public.
Qrator Bot Protection detects brute force activity and blocks traffic from illegitimate IP addresses as soon as they send in their initial request, preventing its execution on the side of the server.
- DOM Inspection
- Javascript Fingerprinting
- Behavioural Analysis
- Search for Tampering
- Scoring against Valid Users
- Measuaring Likeness to Known Bots
The advanced approach of Qrator Bot Protection
Qrator Bot Protection distinguishes good and bad bot traffic without posing inconvenience for legitimate users and bringing comprehensive protection against automated content search, data scraping, brute-force attacks, and DDoS attacks.
- built-in element of the Qrator Labs DDoS Mitigation Solution
- takes minutes to deploy and enables the flexible configuration of user-defined rules
- protects websites, mobile apps and APIs
How Qrator Bot Protection works
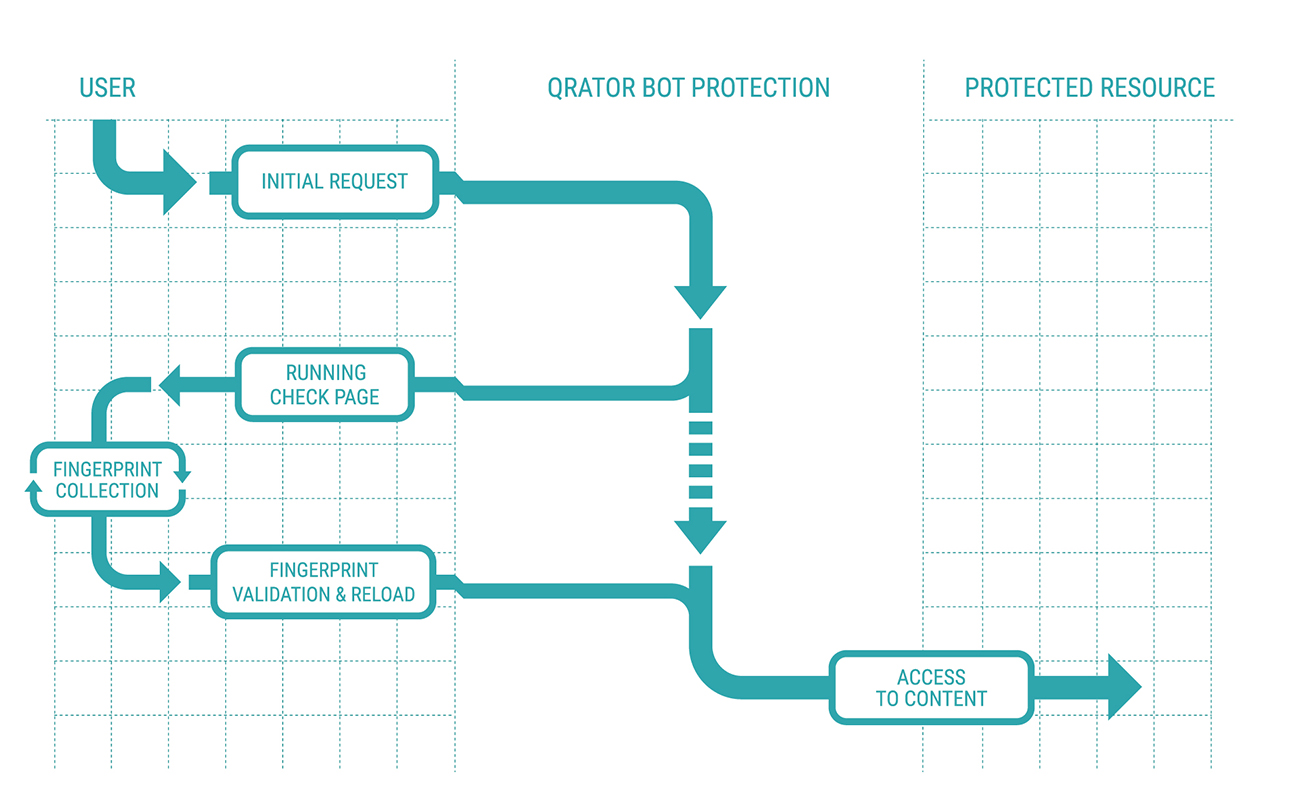
Qrator Bot Protection is included in the delivery set of the Qrator Labs DDoS Mitigation platform and can be turned on and set up in a special section of the Qrator UI.
For the locations where the protected location expects Web-based users, Qrator Bot Protection checks the environment of a browser addressing a protected resource and generates a tracking cookie for browsers considered trusted. At the same time, Qrator Bot Protection restricts access to the resource for visitors who run script-based bots and/or utilize web scraping software suites, including full-stack browser-based solutions.
For the APIs used by native mobile app users (iOS & Android), Qrator Bot Protection supports several protection methods:
- enabling browser-based authentication (BBA) for app users on the login stage, checking the environment and the OS-defined browser used to perform BBA;
- validating security tokens with which the users have to sign their requests
- filtering out the attempts to access the API directly.
Customization for your business
Qrator Bot Protection checks can be set up and customized in the following steps:
- Define the locations of your website where the users should confirm their authenticity by processing the check page: the entry points for your legitimate visitors
- Specify the locations of your website available only for validated users – crucial API calls, credentials fill-in forms, search methods etc.
- Outline your trusted users and friendly bots by using header-based, IP/CIDR-based and geo-based exceptions
- Choose the percentage of your user base affected by the set rules to conduct A/B tests and smoothly onboard the feature
Two operation modes
MONITORING MODE
Qrator Bot Protection proxies a user’s request further in case of any validation result. If a browser sends any response to the Qrator Bot Protection, it will not receive an error code, but validation details will be recorded in the event log. The event log can be viewed anytime by the Qrator Bot Protection operator.
BLOCKING MODE
Badly fingerprinted browsers or applications without JS support (including scrapers without the usage of browsers) will receive a customizable block page. A legitimate user will briefly see the check page first (a blank or a customized 401 page) and, after validation, will get the requested page
The product’s interface supports permissions for good bots, QA and other cases requiring bypassing the checks. Trusted IP addresses, CIDR lists, geozones and header rules can be specified to set up these scenarios.