DNS Qrator.SecondName
DNS is a vital component of the Internet infrastructure for any business. Yet despite being one of the most vulnerable elements susceptible to DDoS attacks, DNS hardening often turns out to be overlooked.
Why are attacks against DNS so dangerous?
Instead of attacking the website itself, attackers can target the availability and stability of a network’s DNS server containing IP addresses for every website on the Internet. In case of an attack against DNS, users' browsers might not be able to determine the target domain’s IP address, which will make a website unavailable. An attacker can constantly generate DNS queries for the DNS server in order to overload its resources.
Without special protection, the only way to mitigate such an attack is to increase server power. However, a constant increase in capacity may result in leveraging the DNS server for carrying out further DDoS attacks on other resources. Failure of a DNS server can lead to partial or complete unavailability of a web resource.
Best-in-class DNS protection
Distributed and reliable cloud DNS Qrator.SecondName is an integral part of our enterprise solution for business’s continuous online availability.
DNS Qrator.SecondName provides minimal response time and a high level of protection against even the most complex and high-speed DDoS attacks.
DNS Qrator.SecondName Key Benefits
 |
Takes seconds to deploy with the unique Reverse Proxy feature |
 |
Truncate functionality protects enterprise DNS servers against IoT-based DDoS attacks |
 |
Qrator Labs anycast network reduces DNS query latency |
Make your DNS server available 24/7
There is no need to install additional software or purchase hardware. Our global anycast network ensures high availability at no additional cost, and in case of an attack against DNS, at least one server remains up and constantly running.
It implements advanced mitigation techniques for attacks against DNS, and a special bot request processing logic working differently from the logic of handling legitimate user requests.
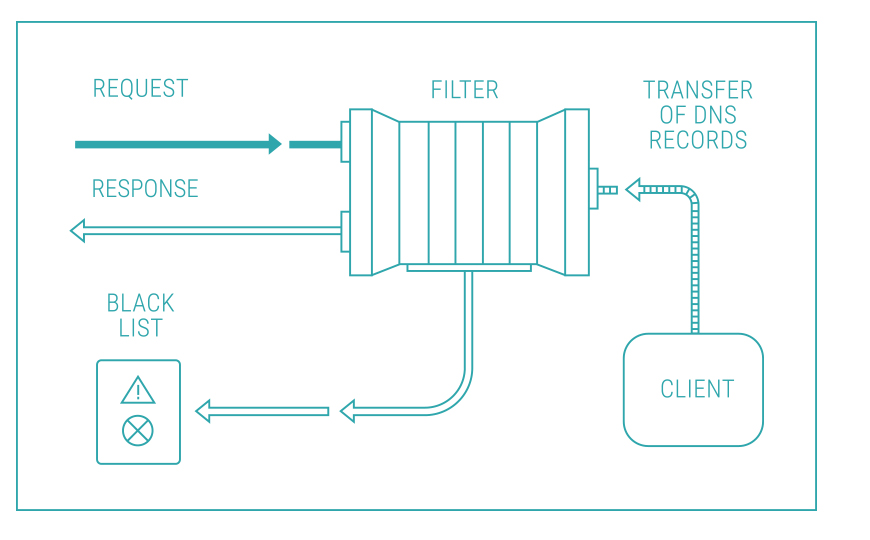
Configure DNS security by choosing one of two implementation options: Qrator Secondary DNS (protection with full disclosure of a domain zone) or Qrator DNS Reverse Proxy (protection without full disclosure of a domain zone).
The DNSSEC protocol is a DNS Security Extension created to increase the security level of DNS record authentication through the use of digital signatures. DNS Qrator.SecondName provides built-in support of DNSSEC to minimize risks of attacks and improve data integrity.
Advanced DNS traffic analytics is always available online in the Qrator Labs dashboard. Customers can generate detailed DNS statistics reports in their personal accounts filtered by response statuses, request types, etc.
How to connect DNS Qrator.SecondName
Qrator Secondary DNS (protection with full disclosure of a domain zone)
- A client allows the transfer of his domain zone from the current NS server to the Qrator Labs’ ns.qrator.net server.
- A client specifies an IP address allocated by Qrator Labs as the authoritative server address for its zone.
- Qrator Labs configures the transfer of a domain zone file from the main client’s NS server whose address is no longer known to attackers (Hidden Primary).
Qrator Secondary DNS (protection without full disclosure of a domain zone)
- Applicable when a client does not have an opportunity to provide control for a domain zone.
- A client reports Qrator Labs on IP address(-es) of authoritative servers (or a Hidden Primary NS server) and specifies an IP address allocated by Qrator Labs as the address of an authoritative server for their own zone.
- With this connection scenario, Qrator Labs NS server will act as a recursor server with a cache of data about a client's connected zone.
- If the Qrator Labs server does not have information about a record, it will send a request to an upstream server and keep a response.