DDoS attacks mitigation
DDoS attacks mitigation
Qrator Labs' filtering network allows small and large businesses to protect their applications from all types of DDoS attacks, regardless of bandwidth or complexity.
15 traffic filtering centers provide excellent network connectivity globally with a throughput of more than 3,000 Gbps.
Qrator Labs advantages
Mitigating attacks at all ISO OSI layers, including L7. The Qrator Labs network automatically provides security up to and including the L7 (application layer) on all billing plans and for all customers.
Easy connection. Qrator Labs provides multiple connection options, including DNS and BGP, with the latter allowing protection of every piece of infrastructure against any attack.
Always-on 24/7 automatic protection. Qrator Labs neither requires constant involvement of qualified specialists nor manual configuration to protect against complex DDoS attacks.
Easy integration with mobile apps and APIs. The advanced API (Application programming interface: https://api.qrator.net/) provides a wide range of features: for example, the client can adjust blacklists and whitelists on the Qrator Labs’ network.
Transparency for legitimate users. We don't use CAPTCHA or other checks that would annoy visitors.
24/7 technical support. Customers can count on Qrator Labs' highly qualified engineers to help them through various communication channels.
A guaranteed level of application availability. The client is not paying for the service if the SLA level has not been met and the service does not meet the declared quality.
Key features of Qrator Labs network technology
- Throughput of more than 3000 Gbps
Qrator Labs' total channel capacity and computing power of the nodes are enough to analyze and process more than 3,000 Gb of traffic per second.
- 15 points of presence around the globe
Direct connection to backbone providers (Tier-1 ISPs). Excellent connectivity in North America, Europe, the Middle East, and Asia.
- Unique BGP-Anycast architecture
BGP-Anycast guarantees a reliable, geographically distributed, and fault-tolerant network to protect applications with a high degree of connectivity. Failure of any filtering node will have no impact on the quality of service and performance of customers' applications due to traffic balancing between major Internet service providers.
- HTTPS traffic protection without disclosure of encryption keys (PCI DSS ready)
Qrator Labs technology makes it possible to analyze and filter HTTPS traffic without providing any encryption keys. For this purpose, client access log analysis and blacklisting and whitelisting policies configurable with Qrator API are used. Legitimate traffic is tunneled to the protected server without decryption or modification. This scheme guarantees the confidentiality of data passing through the Qrator Labs’ network without violating security policies.
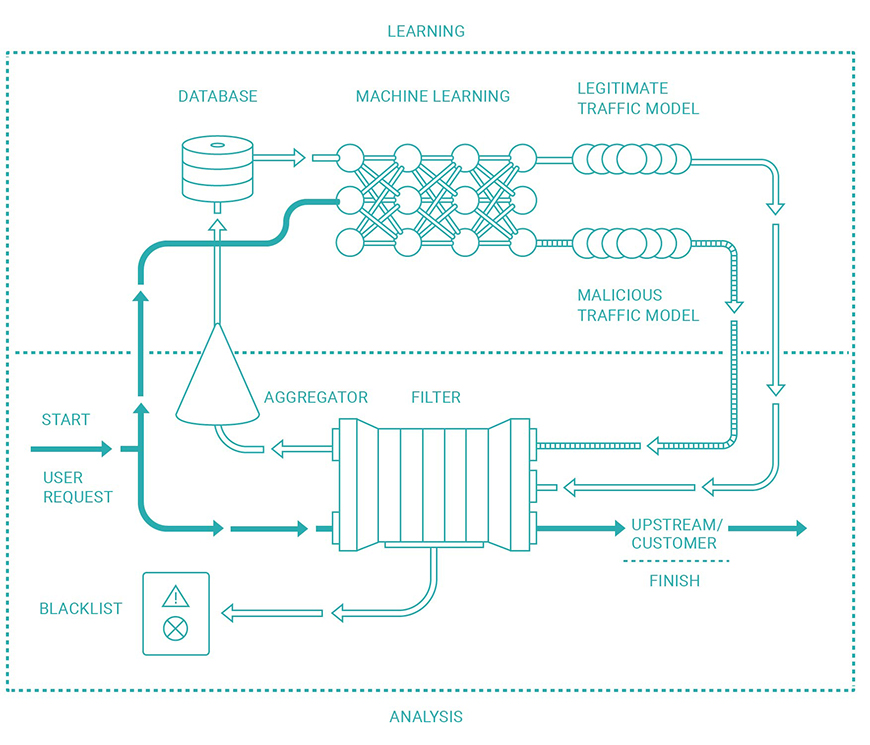
The three main levels of traffic filtering
1. Traffic redirection from the protected application to the Qrator Labs network. Traffic is analyzed at all protocol stack layers, including the application layer (the seventh layer of the OSI model).. The traffic of application-level attacks closely resembles the activity of ordinary users, which makes such attacks very hard to detect and neutralize.
2. Multilayer traffic filtering using behavioral, heuristic, and signature algorithms. By continuously studying the traffic patterns regardless of the presence of DDoS attacks, Qrator Labs improves the algorithms and makes on the fly adjustments to the available filtering methods, allowing it to detect any anomalies and respond immediately to a DDoS attack.
3. Directing clean traffic to the protected application. The filtered traffic is forwarded to the protected application either through the public Internet or through a specially deployed L2 VPN. DDoS attack traffic is blocked at the perimeter of the Qrator Labs network, never reaching the client's resources. Qrator Labs network operation is completely invisible, both to the business and its application’s visitors, and Qrator Labs clients will eventually learn about the attack only from the reports in their personal dashboard.
SLA 100% for Qrator Labs platform availability.
Free 7-day trial period
You get a 7-day trial period in case your application is not under a DDoS attack, or a 1-day trial period if you come under attack.
The average availability of Qrator Labs customers' applications in 2020 - 99,9875%
We increase the level of average availability of our customers' resources each year, backing words with financial guarantees - if the terms of SLA are not met during a month, you will not be charged for our services provided for that month.
Comprehensible online reports in Personal Dashboard
You can access the results of the analysis of your application's traffic for any period you've been using our services.
Integration with monitoring systems
Using the API, you can connect your existing SOC / monitoring system / SIEM with Qrator Labs and receive notifications on the incidents in the format most convenient for you.
Minimum false-positive incidents: no more than 5% during an attack
The algorithms implemented by Qrator Labs allow the determination of the cause for increasing resource attendance - whether it is a DDoS attack or rising interest from the visitors.
Qrator Labs reaction time to a DDoS attack - up to 30 seconds in 97% of attacks vectors